Difference between revisions of "Two-Factor Authentication"
(→Why do you need it?) |
|||
| (33 intermediate revisions by 10 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | Two-Factor Authentication adds a layer of security by adding a second step to the login process. It takes something you know (for example, your password) and adds a second factor, typically from something you have (such as your phone). Requiring both to log in decreases the threat of a leaked password. | |
| − | + | You can access this feature at '''Configuration (<i class="fa fa-wrench" aria-hidden="true"></i>) > System Settings > Two-Factor Authentication''' or, prior to WHMCS 8.0, '''Setup > Staff Management > Two-Factor Authentication'''. | |
| − | === | + | WHMCS includes three Two-Factor Authentication services. |
| + | |||
| + | ===Time-Based Tokens=== | ||
| + | |||
| + | With Time-Based Tokens, you enter a 6-digit code that regenerates every 30 seconds in addition to your regular username and password. Only your token device (typically a mobile smartphone app) will have your secret key and be able to generate valid one-time passwords for your account. | ||
| − | + | We recommend enabling Time-Based Tokens, and WHMCS enables this by default. | |
| − | + | ||
| + | ===DuoSecurity=== | ||
| + | |||
| + | With DuoSecurity, the system will prompt you for a phone number. It will then prompt you to verify your identity using a push notification on your mobile device. | ||
| + | |||
| + | <div class="docs-alert-info"> | ||
| + | * Duo has announced that support for the previous iframe-based Duo Prompt will [https://duo.com/docs/universal-prompt-update-guide end on March 30, 2024]. Duo Security will '''not''' function in WHMCS 8.8 and earlier after this date. | ||
| + | * After you upgrade to WHMCS 8.9 or later, we recommend activating [https://guide.duo.com/universal-prompt Duo Universal Prompt] in your Duo customer portal to ensure continued functionality. | ||
| + | </div> | ||
| + | |||
| + | For more information, see [[Duo Security]]. | ||
| + | |||
| + | ===YubiKey=== | ||
| + | |||
| + | YubiKey creates a one-time password in a USB drive that acts as a keyboard to your computer. These are physical devices that you must purchase [https://www.yubico.com/ from Yubico directly]. | ||
| + | |||
| + | ==Enabling Two-Factor Authentication== | ||
| + | |||
| + | [[File:2FA_006.png|thumb|Time Based Tokens Configuration]] | ||
| + | |||
| + | To enable Two-Factor Authentication, follow the steps below: | ||
| − | + | # Click '''Activate''' under the service that you would like to enable. | |
| + | # Select one or both of '''Enable for use by Clients''' and '''Enable for use by Administrative Users'''. | ||
| + | # If applicable, configure any additional '''Configuration Settings'''. | ||
| + | # Click '''Save'''. | ||
| + | |||
| + | You can repeat these steps for each service that you want to enable. | ||
| + | |||
| + | [[File:2FA_001.png|border|800px]] | ||
| + | |||
| + | ===Global Two-Factor Authentication Settings=== | ||
| + | |||
| + | The '''Global Two-Factor Authentication Settings''' options allow you to forcibly enable Two-Factor Authentication for Accounts, Users, and Admins on their next login. | ||
| + | |||
| + | To use this feature, select your options and click '''Save Changes'''. If a user has not yet configured Two-Factor Authentication, the system will force them to the next time they sign in to WHMCS. | ||
| + | |||
| + | [[File:2FA_002.png|border|800px]] | ||
| − | ==== | + | ==Using Two-Factor Authentication== |
| − | + | ||
| + | Client accounts, users, and admins can begin to use Two-Factor Authentication after you have activated one or more services and configured the installation. | ||
| − | + | For more information, see [[Using Two-Factor Authentication]]. | |
| − | ==== | + | ==Lost/Unavailable Device== |
| − | |||
| − | + | [[Two-Factor Authentication]] requires a secondary device in order to log in. Because of this, some users will inevitably need help when their device is lost or otherwise unavailable. | |
| − | + | For more information, see [[Logging In Without Your Two-Factor Authentication Device]]. | |
| − | ==== | + | ==Troubleshooting== |
| − | + | ||
| + | ====The code you entered did not match what was expected. Please try again.==== | ||
| + | |||
| + | Seeing this error when using the Time-Based Token method means that the six characters your device generated do not match the six numbers WHMCS expected. Usually, this indicates that the time on your device (for example, your phone or tablet) and on the WHMCS server are different. | ||
| + | |||
| + | You can see the time in the top-right corner of your WHMCS Admin Area. It's taken directly from your server's PHP configuration. You must ensure the server time is correct and the time on your device matches the server time. For example, if the server time is 00:01 and the time on your device is 00:00, you will see this error. In that scenario, you must change the time on your device to 00:01 so that they both match. | ||
| + | |||
| + | Syncing the server with [http://en.wikipedia.org/wiki/Network_Time_Protocol NTP] to ensure the time is exactly right may also help to resolve this. Most servers will revert to the internal hardware clock on boot or reboot, so you will need to sync any changes from NTP to the hardware clock. | ||
| + | |||
| + | This provides support for time zone differences, so they are unlikely to cause problems. | ||
| + | |||
| + | ====The second factor you supplied was incorrect. Please try again.==== | ||
| − | + | Seeing this error when activating the DuoSecurity method for the first time indicates that the entered code does not match what DuoSecurity expects. This indicates that the time on your server does not match DuoSecurity's clocks. | |
| − | + | ||
| − | + | You can see the time in the top-right corner of your WHMCS admin area. It's taken directly from your server's PHP configuration. You must make sure to sync the server time exactly with UTC. For example, if the server time is 00:01 and the time at DuoSecurity is 00:00, you will see this error. | |
| − | + | ||
| − | + | Syncing the server with [http://en.wikipedia.org/wiki/Network_Time_Protocol NTP] to ensure the time is exactly right will resolve this. Most servers will revert to the internal hardware clock when they boot or reboot, so you will need to sync any changes from NTP to the hardware clock. | |
| − | + | ||
| − | + | This provides support for time zone differences, so they are unlikely to cause problems. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | [ | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Latest revision as of 17:04, 7 February 2024
Two-Factor Authentication adds a layer of security by adding a second step to the login process. It takes something you know (for example, your password) and adds a second factor, typically from something you have (such as your phone). Requiring both to log in decreases the threat of a leaked password.
You can access this feature at Configuration () > System Settings > Two-Factor Authentication or, prior to WHMCS 8.0, Setup > Staff Management > Two-Factor Authentication.
WHMCS includes three Two-Factor Authentication services.
Contents
Time-Based Tokens
With Time-Based Tokens, you enter a 6-digit code that regenerates every 30 seconds in addition to your regular username and password. Only your token device (typically a mobile smartphone app) will have your secret key and be able to generate valid one-time passwords for your account.
We recommend enabling Time-Based Tokens, and WHMCS enables this by default.
DuoSecurity
With DuoSecurity, the system will prompt you for a phone number. It will then prompt you to verify your identity using a push notification on your mobile device.
- Duo has announced that support for the previous iframe-based Duo Prompt will end on March 30, 2024. Duo Security will not function in WHMCS 8.8 and earlier after this date.
- After you upgrade to WHMCS 8.9 or later, we recommend activating Duo Universal Prompt in your Duo customer portal to ensure continued functionality.
For more information, see Duo Security.
YubiKey
YubiKey creates a one-time password in a USB drive that acts as a keyboard to your computer. These are physical devices that you must purchase from Yubico directly.
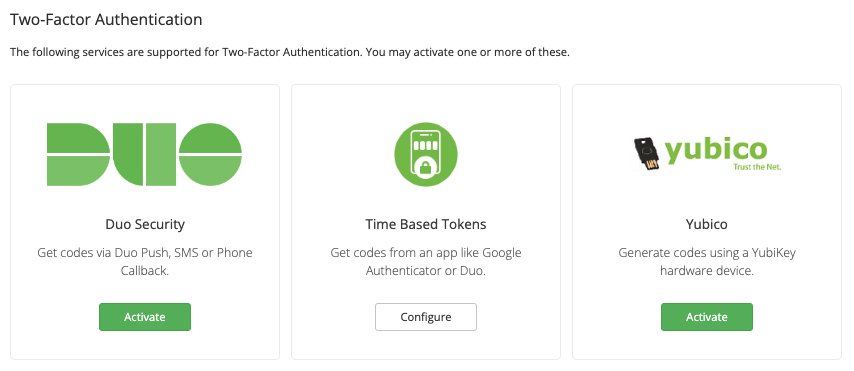
Enabling Two-Factor Authentication
To enable Two-Factor Authentication, follow the steps below:
- Click Activate under the service that you would like to enable.
- Select one or both of Enable for use by Clients and Enable for use by Administrative Users.
- If applicable, configure any additional Configuration Settings.
- Click Save.
You can repeat these steps for each service that you want to enable.
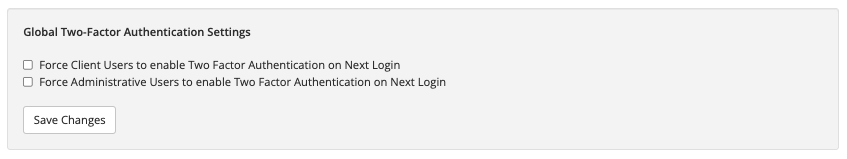
Global Two-Factor Authentication Settings
The Global Two-Factor Authentication Settings options allow you to forcibly enable Two-Factor Authentication for Accounts, Users, and Admins on their next login.
To use this feature, select your options and click Save Changes. If a user has not yet configured Two-Factor Authentication, the system will force them to the next time they sign in to WHMCS.
Using Two-Factor Authentication
Client accounts, users, and admins can begin to use Two-Factor Authentication after you have activated one or more services and configured the installation.
For more information, see Using Two-Factor Authentication.
Two-Factor Authentication requires a secondary device in order to log in. Because of this, some users will inevitably need help when their device is lost or otherwise unavailable.
For more information, see Logging In Without Your Two-Factor Authentication Device.
Troubleshooting
The code you entered did not match what was expected. Please try again.
Seeing this error when using the Time-Based Token method means that the six characters your device generated do not match the six numbers WHMCS expected. Usually, this indicates that the time on your device (for example, your phone or tablet) and on the WHMCS server are different.
You can see the time in the top-right corner of your WHMCS Admin Area. It's taken directly from your server's PHP configuration. You must ensure the server time is correct and the time on your device matches the server time. For example, if the server time is 00:01 and the time on your device is 00:00, you will see this error. In that scenario, you must change the time on your device to 00:01 so that they both match.
Syncing the server with NTP to ensure the time is exactly right may also help to resolve this. Most servers will revert to the internal hardware clock on boot or reboot, so you will need to sync any changes from NTP to the hardware clock.
This provides support for time zone differences, so they are unlikely to cause problems.
The second factor you supplied was incorrect. Please try again.
Seeing this error when activating the DuoSecurity method for the first time indicates that the entered code does not match what DuoSecurity expects. This indicates that the time on your server does not match DuoSecurity's clocks.
You can see the time in the top-right corner of your WHMCS admin area. It's taken directly from your server's PHP configuration. You must make sure to sync the server time exactly with UTC. For example, if the server time is 00:01 and the time at DuoSecurity is 00:00, you will see this error.
Syncing the server with NTP to ensure the time is exactly right will resolve this. Most servers will revert to the internal hardware clock when they boot or reboot, so you will need to sync any changes from NTP to the hardware clock.
This provides support for time zone differences, so they are unlikely to cause problems.